- Blog
What is domain spoofing and how does it work?

Oliver Kampmeier
Cybersecurity Content Specialist

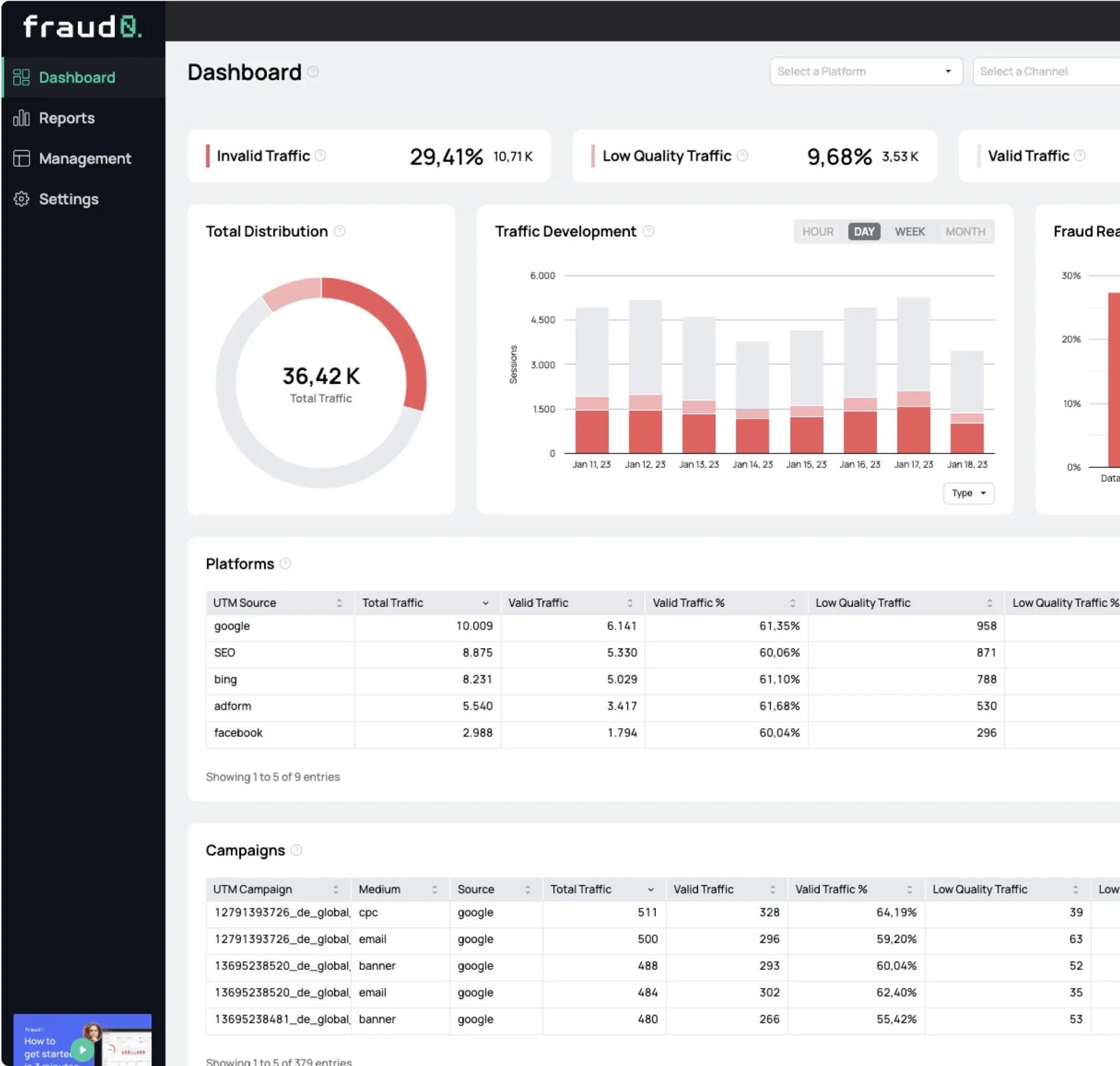
For an advertising campaign to be successful, advertisers need to ensure that their ad budget is used in the best possible way and reaches as many real people as possible. But fraudsters are lurking everywhere, and so there are a variety of players who want to skim off some of the ad budget.
One fraud technique that has been popular for years is so-called “domain spoofing”. In the following article, you will learn exactly what it is, what different forms it takes, and how you as an advertiser can protect your ad budget from it.
What is domain spoofing and how does it work?
Domain spoofing is a widespread technique used by fraudsters to siphon off ad budget. It involves creating low-quality websites that pretend to be well-known websites and are often an exact copy of them. At first glance, the fake website is very difficult to distinguish from the original.
Fraudsters submit the fake websites to various advertising networks, pass them off as premium inventory and include display and video ads on them. Then, they use bot traffic that interacts with the ads to eventually receive a payout.
The approach sounds simple and effective, and it is. Advertisers pay for this supposed premium traffic, but never see a conversion or the hoped-for branding effects.
There are many reasons why domain spoofing is used:
- To commit ad fraud through low-quality or automated bot traffic
- To disguise the origin of traffic if the website has illegal or unwanted content
- To commit phishing
- To spread malware / spyware
- To steal personal information
What are the different types of domain spoofing?
Domain spoofing can be divided into simple and more complex methods.
Simple domain spoofing methods involve spoofing websites by copying them 1:1 and making them available under a new domain.
More complex methods include spoofing an email address, spreading malware through a website, or stealing personal information.
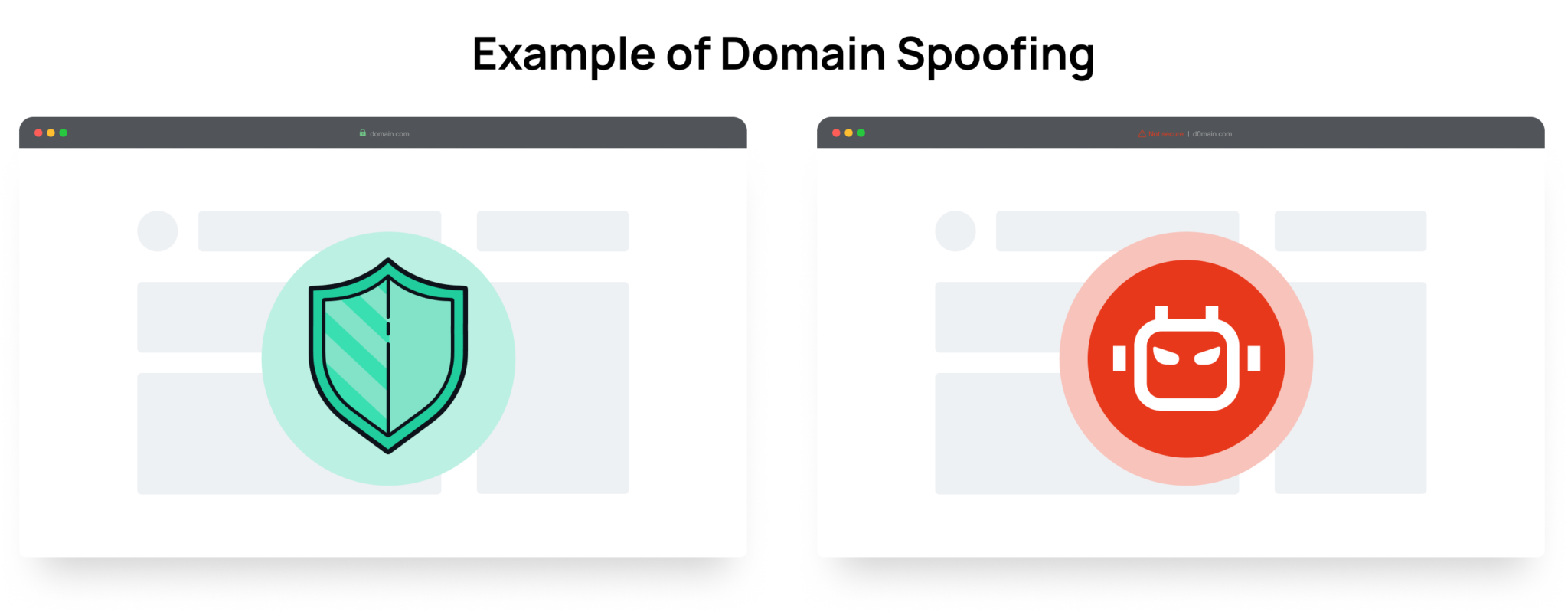
Website / URL Spoofing
The simplest type of domain spoofing. Fraudsters submit a URL of a real, high-value publisher to the ad server. Advertisers think their ad was served on a real website like forbes.com, but in reality the ad was served on a fake website.
Another way fraudsters can mimic a legitimate website is by using Unicode characters in the domain. Unicode is an international standard for character encoding that provides a unique number for each character in all languages and scripts, making almost all characters accessible across platforms, programs and devices.
For example, the letter “h” is virtually indistinguishable from the Unicode character “һ” (Shha in Unicode). Fraudsters take advantage of this and register domains for their fake websites that resemble the domain name of legitimate websites.
A list of visually similar Unicode characters can be found here.
Cross-domain embedding
This method makes use of iFrames. An iFrame is an HTML element that can be used to embed external content into a website. This content can be e.g. images or videos, but it can also be used to embed entire websites into other websites.
By embedding a high-value website in an iFrame into a fake website, it can look to advertisers as if their ads were served on the higher-value website.
Malware
With the help of infected apps or browser extensions, fraudsters can insert ads into websites and apps without the user’s knowledge.
The way it works is very simple: when a user opens an infected app, invisible advertising banners are loaded in the background, which are then clicked on automatically. Every click on an ad earns the fraudsters money.
One fraud based on this principle was Zacinlo. Among other things, the malware performed fraudulent browser redirects, created fake clicks on online ads in hidden browser windows, and also swapped ads that loaded naturally in the victim’s browser with the attackers’ ads so that they could collect the ad revenue.
Why is domain spoofing still a very big problem in 2023?
To put it simply: because fraudsters can make a lot of money very quickly.
It has never been easier to copy an existing website in an automated way, put ads on it and then make money via bot traffic and fake clicks. How easy it is even for not too tech-savvy people was impressively captured by a CNBC reporter some time ago. Within a few days, she was able to monetize her fake website on various advertising networks.
In 2017, the Financial Times investigated the extent of fake domains impersonating themselves on various advertising networks. The result: the value of fraudster ad inventory was about $1.3 million a month.
Methbot was one of the largest ad fraud schemes a few years ago. At its peak, it faked up to 400 million video ad views, 6,000 domains, and over 250,000 URLs per day. The fraudsters were able to earn up to $3 million a day this way, including through domain spoofing.
In our overview of the biggest ad fraud cases of the last few years, it quickly becomes clear that domain spoofing is very high on the list as a fraud technique, and countless fraudsters have already made millions with it.
Tips for detecting domain spoofing
Domain spoofing can quickly drain your ad budget. Below are some tips on how to detect domain spoofing.
Manually review reports
Regularly review your placement reports and look for inconsistencies in domain names and URLs. This could be extra letters or digits. You should pay special attention to the previously mentioned Unicode characters, which can be easily confused with other letters.
However, a manual check is in most cases very laborious and time-consuming, especially for large advertising campaigns.
Therefore, it is recommended from the start to place ads only on selected domains that have been previously specified in an Allow / Inclusion list.
Use Ads.txt
Launched in May 2017 by the IAB Tech Lab, the Authorized Digital Sellers project aims to combat various types of ad fraud, most notably domain spoofing and illegal inventory arbitrage.
Ads.txt is a simple text file that contains information about which companies are allowed to sell digital inventory on a given domain. Since it can be created and modified only by a domain’s webmaster, the file’s information is considered valid and authentic.
Even though an existing ads.txt file cannot stop domain spoofing 100%, it still provides another layer of protection – provided the file has been implemented correctly by the publisher and is maintained regularly.
So, place your ads only on domains that have an ads.txt file present.
Use of fraud detection software
Both manual measures and the use of ads.txt can only protect you to a limited extent in the fight against domain spoofing. Unfortunately, this cannot protect you from all attacks such as cross-domain embedding.
That is why we recommend you to use a fraud detection software that will protect you from domain spoofing and many other frauds in real time.
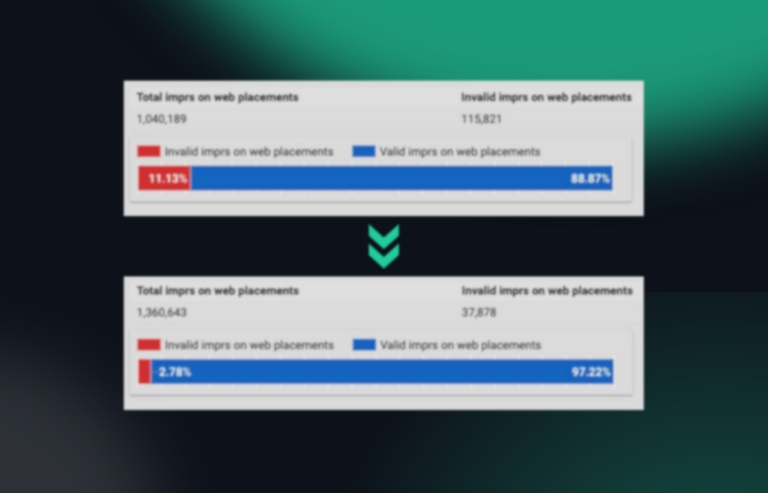
fraud0 protects you from domain spoofing by analyzing various characteristics of the domain. Among other things, our system can determine whether the ad is displayed in an iFrame (including reporting of the iFrame as well as the main URL) and whether the transmitted URL is actually the URL on which the ad was served.
In addition, our system also prevents you from placing your ads next to unsafe and inappropriate content (e.g. fake news, radical political content, terrorist or sexually sensitive websites) and thus protects your brand reputation.
See for yourself and sign up for a free 7-day trial.
- Published: June 7, 2023
- Updated: July 2, 2025

See what’s hidden: from the quality of website traffic to the reality of ad placements. Insights drawn from billions of data points across our customer base in 2024.
1%, 4%, 36%?