- Blog
Device Spoofing – What it is and how to protect your ad budget

Oliver Kampmeier
Cybersecurity Content Specialist

Fraudsters will use a variety of strategies to perform their scams. One of the most common and most used strategy fraudsters use to conceal their illegal actions and obscure their identities is device spoofing.
Device spoofing is a method that cybercriminals employ to trick systems, networks, and devices into believing that their device is authentic. It involves changing a device’s identity to imitate another device or user, such as a computer or mobile phone.
Device spoofing is typically done to launch phishing attacks, gain unauthorized access to sensitive data or resources, or in the case of ad fraud to avoid detection by security systems and to avoid digital fingerprinting.
In this article, we will discuss device spoofing in detail, including the techniques used by attackers, the types of device spoofing, and how to protect yourself from it.
How Device Spoofing works
Device spoofing works by manipulating a device’s unique identifiers, such as:
- Media Access Control (MAC) address
Changing the MAC address of a device to appear as a trusted device on a network. - Internet Protocol (IP) address
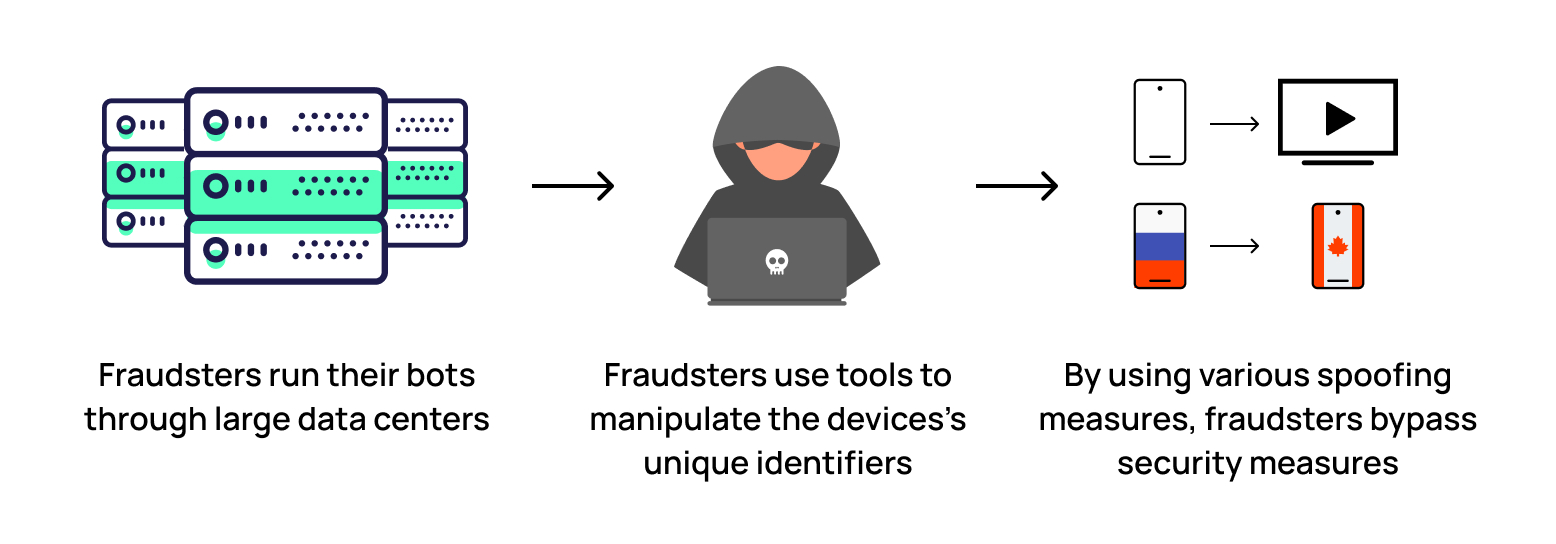
Spoofing a device’s IP address to trick a network or system into accepting it as a legitimate device. Fraudsters run their bots through large Amazon, Google, or Microsoft data centers. However, their IP addresses are blocked by bot detection software, so fraudsters disguise the bots’ IP addresses and often pass them off as a residential IP address. - Global Positioning System (GPS)
location Manipulation of the GPS signal to provide false location information to deceive location-based services. Using fake GPS data, fraudsters also manage to get geographically restricted ads displayed. - User-Agent String (UA String)
By manipulating the user agent string, fraudsters can impersonate a particular browser. This method is especially common in connection with CTV fraud. Fraudsters use a headless version of Chrome running in a data center for their bots and impersonate Connected TV (CTV), to display more expensive video ads. - Caller ID
Falsifying the caller ID information to hide the true identity of the caller. - Technical device details
Fraudsters can also manipulate all the technical details of a device. This includes graphics card info, CPU info, IMEI, unique Android and / or Apple ID, the version of the operating system and many more.
How is device spoofing used for ad fraud?
By using various spoofing measures, fraudsters can bypass a number of security protocols. To identify who is using their services or visiting their websites, for instance, many ad platforms or online services will use device fingerprinting.
Device fingerprinting uses a variety of techniques, including a combination of the user agent string and other factors like the IP address, device hash, cookie hash, and more, to identify the website visitor.
Device fingerprinting can also be used to block the display of ads from specific browsers, device types, or even geographic areas.
With the help of device spoofing, fraudsters manipulate and bypass device fingerprinting. Specifically, they use it to:
- Make a bot look like a real person
- Display ads outside of their geographic location, resulting in higher revenues
- Spoof bots as CTV devices to get paid for higher priced ad inventory
In our overview of the biggest cases of ad / click fraud, the trend is quite clear: fraudsters have been making a killing in recent years by passing off bots as CTV devices to get more expensive ad inventory. Fraudsters have even gone so far as to spoof smart refrigerators as CTVs devices. All thanks to the device spoofing method and a wide range of software that makes it possible.
How to protect yourself from device spoofing
The good news first: With bot detection software like fraud0 it is possible to protect your ad budget from device spoofing.
fraud0 automatically examines several thousand factors in real time for each visitor. The system also uses artificial intelligence (AI) and machine learning (ML) to learn how visitors interact with your website / app, helping you detect and block spoofing attempts.
Now for the bad news: without such software, you won’t be able to detect device spoofing attacks. The fraudsters are too clever for that, and their deployed bots are too advanced. In your analytics data, you would only see traffic coming from what appears to be real devices.
- Published: March 27, 2023
- Updated: July 2, 2025

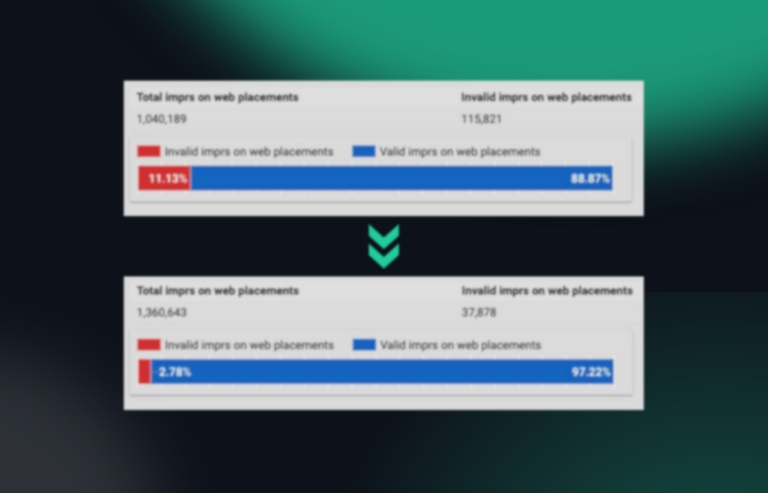
See what’s hidden: from the quality of website traffic to the reality of ad placements. Insights drawn from billions of data points across our customer base in 2024.
1%, 4%, 36%?