- Blog
Inside SlopAds: How 224 Fake Apps Turned 38 Million Phones Into Ad-Bots

Oliver Kampmeier
Cybersecurity Content Specialist

When you download an app from the Google Play Store, you probably do so with a reasonable sense of safety. It’s the official marketplace, vetted by Google, and home to the tools that power our digital lives. But a newly uncovered ad fraud campaign, dubbed “SlopAds,” is a sharp reminder that even the Play Store isn’t immune to sophisticated scams.
Security researchers at Satori Threat Intelligence found a sprawling network of 224 malicious apps that slipped past Google’s defenses and racked up more than 38 million downloads. On the surface, these apps looked harmless. Behind the scenes, they transformed phones into background ad-clicking machines, draining battery, slowing performance, and secretly generating billions of fake ad requests.
Here are the four most devious tricks that made SlopAds so effective at hiding in plain sight.
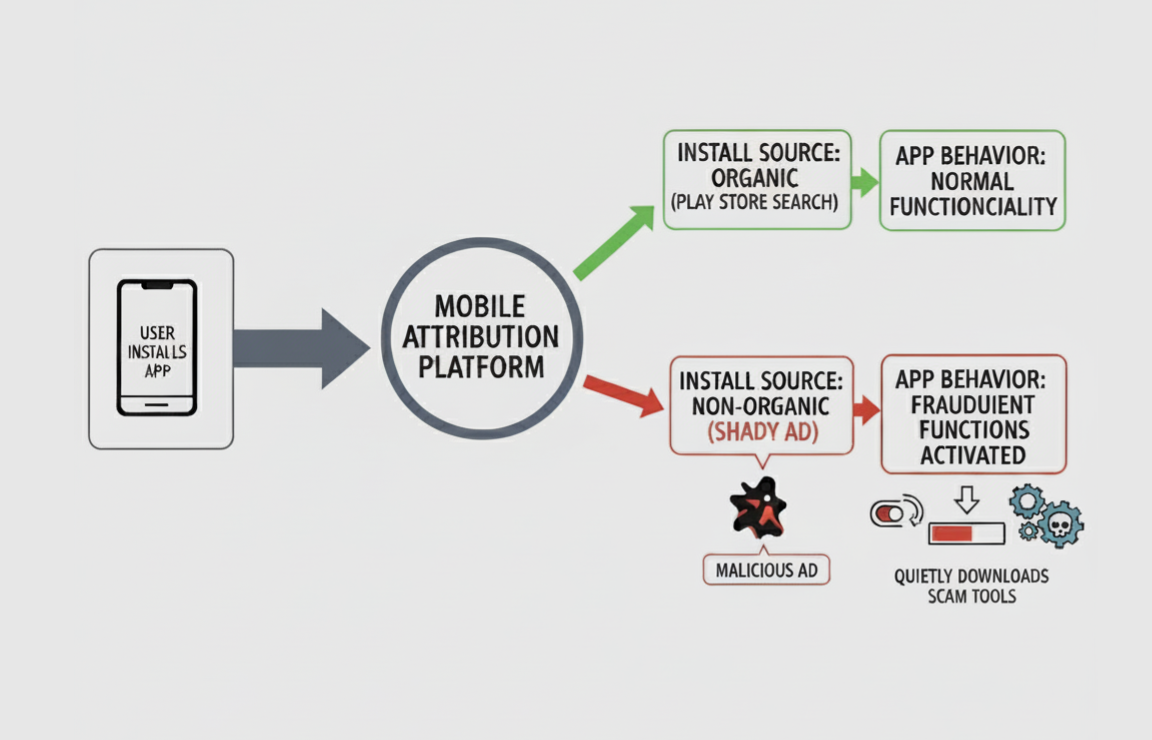
The app knew how you found it and behaved accordingly
One of the cleverest tricks was the app’s ability to detect how it had been installed. By using a mobile marketing attribution platform, a perfectly legitimate tool normally used to track which ads drive installs, the app could see whether it came from a Play Store search (“organic”) or from a shady ad (“non-organic”).
If you found it organically, the app acted completely normal. This helped it pass Google’s security checks and avoid suspicion from researchers. But if it was installed through a malicious ad, the app flipped a switch: it activated its fraudulent functions and quietly started downloading the tools it needed for the scam.
This selective activation made the app nearly invisible to most oversight,a devious abuse of marketing tech.
The malicious payload was hidden in plain sight
SlopAds also used steganography, a technique for hiding data inside something that looks harmless. Once activated, the app contacted its command-and-control (C2) server and downloaded what looked like four regular PNG image files.
Hidden inside those images, however, were the encrypted pieces of the malicious payload. The app stitched them together into an APK file called “FatModule,” which contained all the code needed to carry out ad fraud. To the user, everything looked normal, they were just running a simple app.
The campaign had an ‘AI Slop’ theme
Researchers gave the operation its name for two reasons: the apps looked mass-produced, like “AI slop,” and the infrastructure behind the scam was peppered with AI themes.
When digging into the C2 server, researchers even found knock-off versions of popular AI services hosted by the threat actors. There was evidence of an AI tool being trained on the same domain. It’s unclear if this AI was directly used to run the fraud, but the overlap highlights a growing reality: cybercriminals are experimenting with AI just as much as legitimate businesses.
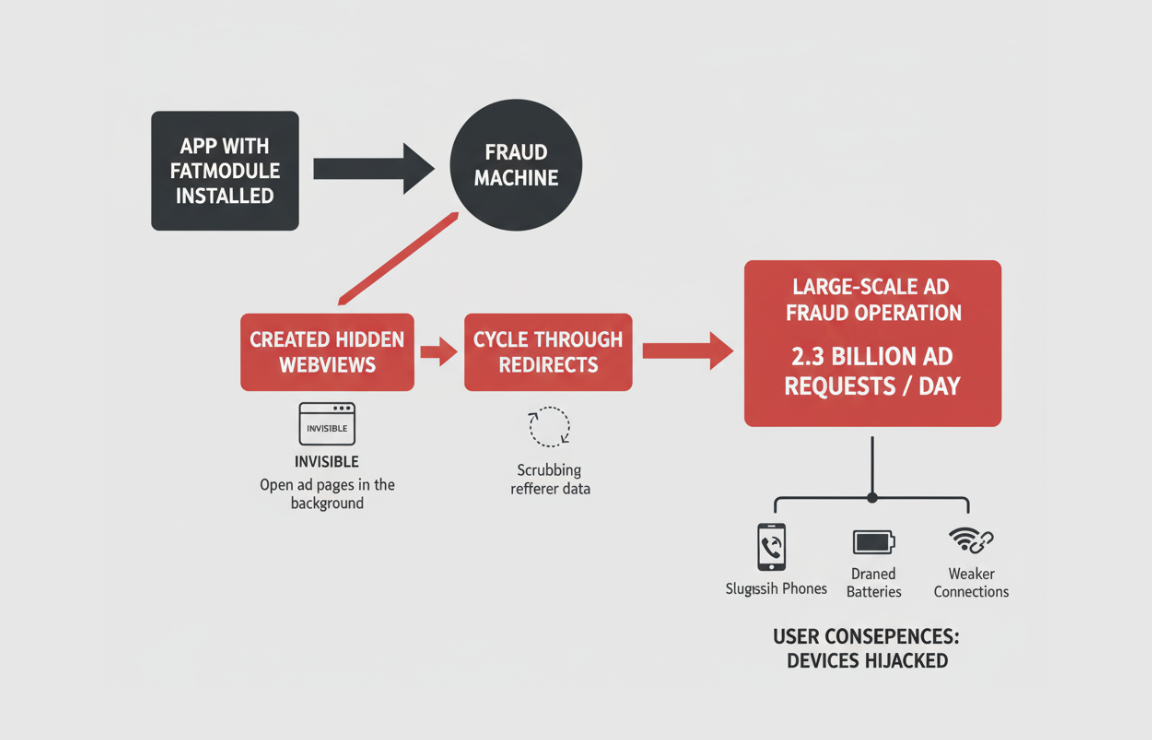
It secretly used your phone to generate billions of fake ad requests
Once the FatModule was in place, the fraud machine went into overdrive. The app created hidden “WebViews”, tiny invisible browser windows, to open ad pages in the background.
To make the traffic look genuine, the app cycled through multiple redirects, scrubbing the referrer data along the way. At its peak, this operation was generating an eye-watering 2.3 billion ad requests per day.
The consequences for users were obvious: sluggish phones, drained batteries, and weaker connections, all because their devices were being hijacked for large-scale ad fraud.
How to protect yourself
Google has removed the known malicious apps, but the scale and sophistication of SlopAds prove just how important it is to stay vigilant. Protection isn’t just for private users, advertisers also need to take precautions.
For Android users
- Check app permissions: Be skeptical of what an app asks for. If a flashlight app wants your contacts, that’s a red flag.
- Research the developer: Look up who made the app. Scammers often mimic legit publishers.
- Delete unused apps: Fewer apps = less exposure.
- Keep your phone updated: Updates often include security patches that block these tricks.
- Use mobile security software: Just like PCs, phones benefit from an extra layer of protection.
For advertisers
- Audit your placements: Regularly review where your ads are being served to ensure they’re not showing up on suspicious apps or sites.
- Use fraud detection tools: Invest in solutions that can spot invalid traffic (IVT) and filter out bot-driven impressions.
- Track unusual patterns: Sudden spikes in impressions or clicks from unknown apps or geographies can signal fraud.
- Work with trusted partners: Stick to transparent networks and demand placement-level reporting.
- Test and verify: Don’t just assume platforms catch everything, independent verification adds another safety net.
Final thoughts
The SlopAds campaign shows how creative and persistent mobile scammers have become. Researchers even uncovered 300+ promotional domains tied to the operation, hinting that the 224 apps discovered might just be the tip of the iceberg.
As fraudsters keep innovating, the definition of a “safe app” is shifting. The Play Store may be the best first line of defense, but it’s not bulletproof. Staying alert, skeptical, and security-minded is the only way to keep your phone from becoming the next cog in a massive ad fraud machine.
- Published: September 25, 2025
- Updated: September 25, 2025

See what’s hidden: from the quality of website traffic to the reality of ad placements. Insights drawn from billions of data points across our customer base in 2024.
Protect Your Data and Analytics From Bots and Invalid Traffic
Take back control over your data and try fraud0.
- 7 days free trial
- No credit card required